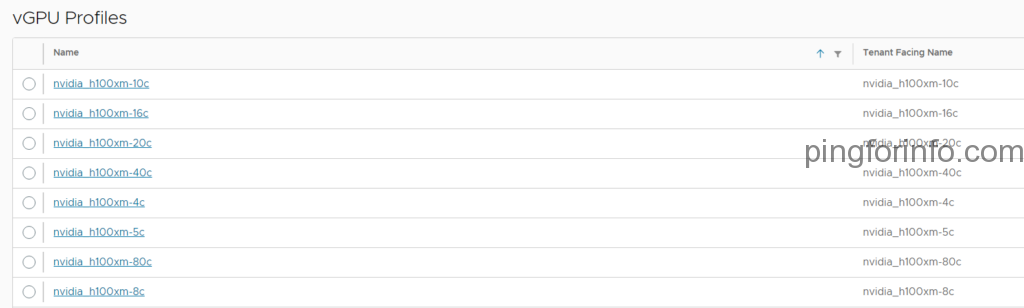
This blog post guides you through uninstalling NVIDIA Enterprise AI drivers from an ESXi 8.0U2 host.

Putting the ESXi Host into Maintenance Mode
Before modifying software configurations, it’s crucial to put the ESXi host into maintenance mode. This ensures no running virtual machines are affected during the process.
Checking Installed NVIDIA Drivers
Once in maintenance mode, SSH to the host and use the following command to identify currently installed NVIDIA drivers:
[root@esx1-sree-lab:~] esxcli software vib list | grep -i NVD
NVD-AIE_ESXi_8.0.0_Driver 535.154.02-1OEM.800.1.0.20613240 NVD VMwareAccepted 2024-03-20 host
nvdgpumgmtdaemon 535.154.02-1OEM.700.1.0.15843807 NVD VMwareAccepted 2024-03-20 hostThe output will display details like driver name, version, and installation date. In the example, the following NVIDIA VIBs are found:
NVD-AIE_ESXi_8.0.0_Drivernvdgpumgmtdaemon
Removing the Driver VIBs
Now, proceed to remove the listed VIBs using the esxcli software vib remove command. Here’s how to remove each VIB:
- nvdgpumgmtdaemon:
[root@esx1-sree-lab:~] esxcli software vib remove -n nvdgpumgmtdaemon
Removal Result
Message: The update completed successfully, but the system needs to be rebooted for the changes to be effective.
VIBs Installed:
VIBs Removed: NVD_bootbank_nvdgpumgmtdaemon_535.154.02-1OEM.700.1.0.15843807
VIBs Skipped:
Reboot Required: true
DPU Results:
This command removes the nvdgpumgmtdaemon VIB. The output will confirm successful removal and indicate a required reboot for changes to take effect.
- NVD-AIE_ESXi_8.0.0_Driver:
[root@esx1-sree-lab:~] esxcli software vib remove -n NVD-AIE_ESXi_8.0.0_Driver
Removal Result
Message: The update completed successfully, but the system needs to be rebooted for the changes to be effective.
VIBs Installed:
VIBs Removed: NVD_bootbank_NVD-AIE_ESXi_8.0.0_Driver_535.154.02-1OEM.800.1.0.20613240
VIBs Skipped:
Reboot Required: true
DPU Results:
Similarly, this command removes the main NVIDIA driver VIB and prompts for a reboot.
Rebooting the ESXi Host
After removing both VIBs, it’s essential to reboot the ESXi host to apply the changes. Use the following command:
[root@esx1-sree-lab:~] rebootThe host will reboot, and the NVIDIA drivers will be uninstalled.
Verifying Uninstallation
Once the ESXi host restarts, confirm that the NVIDIA drivers are no longer present. Use the same command as before to check the installed VIBs:
[root@esx1-sree-lab:~] esxcli software vib list | grep -i NVDIf the output is empty or doesn’t contain any NVIDIA-related entries, the drivers have been successfully uninstalled.
Important Notes:
- This guide serves as a general overview. Always refer to the official documentation for your specific NVIDIA driver version and ESXi host configuration for detailed instructions.
- Putting the ESXi host into maintenance mode is crucial to avoid disruptions to running virtual machines.
By following these steps, you can effectively uninstall NVIDIA Enterprise AI drivers from your ESXi 8.0U2 host